Cybersecurity Services
Cybersecurity is a critical component of all IT, particularly for cloud-based systems. B/Net follows a multi-pronged approach that covers everything from the basics to the highly complex.

We routinely set up multi-factor authentication, harden online systems, and configure secure user access and controls. We also perform penetration testing and mobile device management. Our best-in-class cybersecurity training program educates staff—our clients’ last line of defense—to recognize potential security threats to your IT environment.
Standard Security Services
We set up MFA for all cloud-based accounts. MFA is a system that requires an additional piece of information, besides the username and password, to access an account. This provides an extra layer of security that guards against others hacking into our clients’ online accounts.
We restrict administrator access on workstations to limit the damage that could be done if a computer is compromised.
We use our device management software tool to consistently and continuously apply and monitor security settings on individual computers and mobile devices. We can set alerts to instantly see if systems go out of compliance and can quickly reset them if needed.
We properly configure firewalls and ensure the latest software/firmware updates.
We systematically ensure that servers and workstations have the latest software patches.
We regularly back up all important system files so data is secure in the event of system failure or a security breach.
Enhanced Security Services
B/Net will perform a comprehensive security assessment of your technology environment and provide you with a report that contains the assessment results, the risks if not addressed, a security score comparison (for Office 365 customers) and recommendations. Based on the assessment results, B/Net will draft an actionable security plan to address the needs of your organization.
B/Net will help you comply with the IT security standards requirements for cybersecurity insurance. Higher levels of compliance mean lower insurance premiums for you. From configuring and enforcing MFA to secondary cloud data backups, we can support your cyberinsurance compliance needs.
We also have proven processes to assess our client’s level of regulatory compliance with PCI, HIPAA, GDPR, and others and remediate where needed. B/Net can help you pass an IT audit or remedy poor audit results.
We work with our long-time security partners to scan your network internally to identify security weaknesses that could allow external access. Exploring your network for vulnerabilities enables early intervention and implementation of risk reduction strategies. We offer this service as a standalone assessment or as part of an annual security review.
B/Net works with an experienced IT security partner to perform penetration tests. Probing your network for security vulnerabilities can lead us to early intervention and the implementation of risk reduction strategies. B/Net offers this service as a standalone assessment or as part of an annual security review.
Scan your online applications to ensure that access is restricted to designated users.
Train your staff to follow best practices when using cloud resources, and to identify phishing emails accurately
Social engineering has become the primary method for malware delivery and ransomware attacks. Through a partner program, B/Net can administer a cyber security awareness program for you and your staff. Our annual process has demonstrated consistent success in improving cyber security awareness.
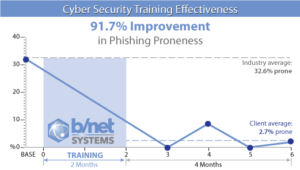
Our white paper “Addressing Your Cyber Security Threat” highlights potential vulnerabilities to phishing and how to improve your company’s online security. A mid-sized association’s recent B/Net cyber security training resulted in a 91.7% phishing proneness improvement.
Our SIEM solution centralizes security information from multiple endpoints, servers, applications, and other sources to monitor IT infrastructure, check for anomalies in real-time, alert security professionals whenever there is an abnormal event, and maintain detailed data logs of all events (anomalous, adverse, or routine).
Is your organization operating in a “sophisticated” IT environment or the “Wild West”?
Check out this new podcast with B/Net Systems’ CEO, Chris Dean as he discusses the critical need for Cybersecurity and more with Alessandro Cutri of Surge Growth.
Get a sneak peek of the engaging discussion here, but for complete conversation, including Cybersecurity “Must Dos”, visit YouTube channel: https://lnkd.in/gh6FM7f4